Because attackers continuously devise new schemes for monetizing hacked machines, cryptojacking has emerged as one of the top ways for cybercriminals to turn hacks into cash.
Pentesters always try to master the dizzying variety of exploits and vulnerabilities. A responsibility to protect our clients obliges us to plug every hole in our clients’ networks before the bad guys do. However, we often neglect the post-exploitation phase of an attack. After an attacker has already pwned a system and spread through the network, what do they do?
The most common way for attackers to monetize a hack is cryptojacking. Cryptojacking simply means mining cryptocurrency illicitly on an unauthorized device. And due to the emergence of “privacy coins,” particularly Monero, cryptojacking offers an untraceable income stream from hacked devices.
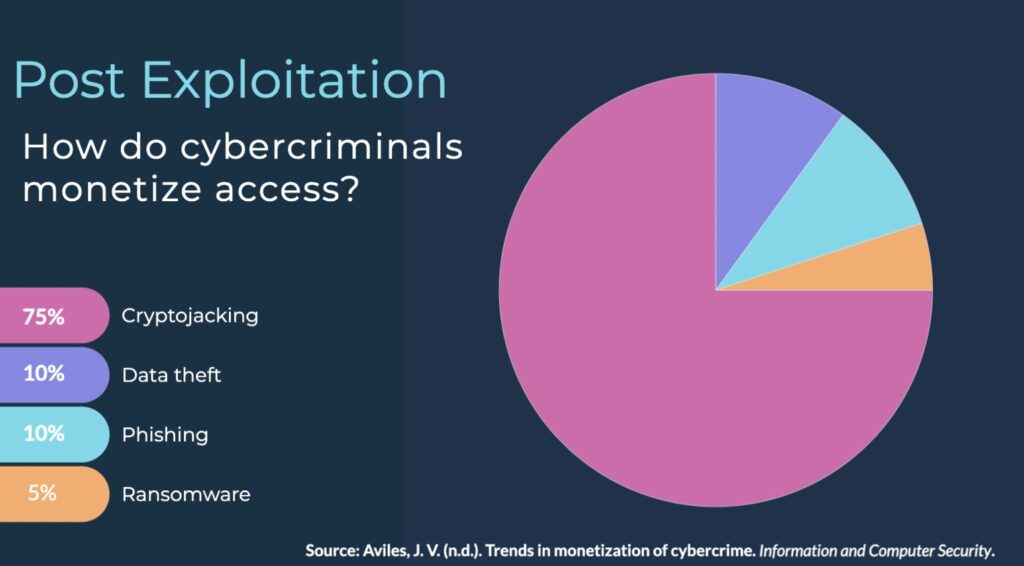
Knowing what attackers are doing with access is a crucial data point when making a good threat model. Aside from being useful to look at things from the attacker’s view, it’s also fun. So let’s dive in!
Make a wallet for cryptojacking funds
When we start mining on the infected machines, we’ll need a Monero address to send the ill-gotten gains to. As white hats, we don’t really need the full privacy power of Monero. Thus, we can use a simpler web wallet.
Let’s try xmrwallet.com, one of the most beginner-friendly options.
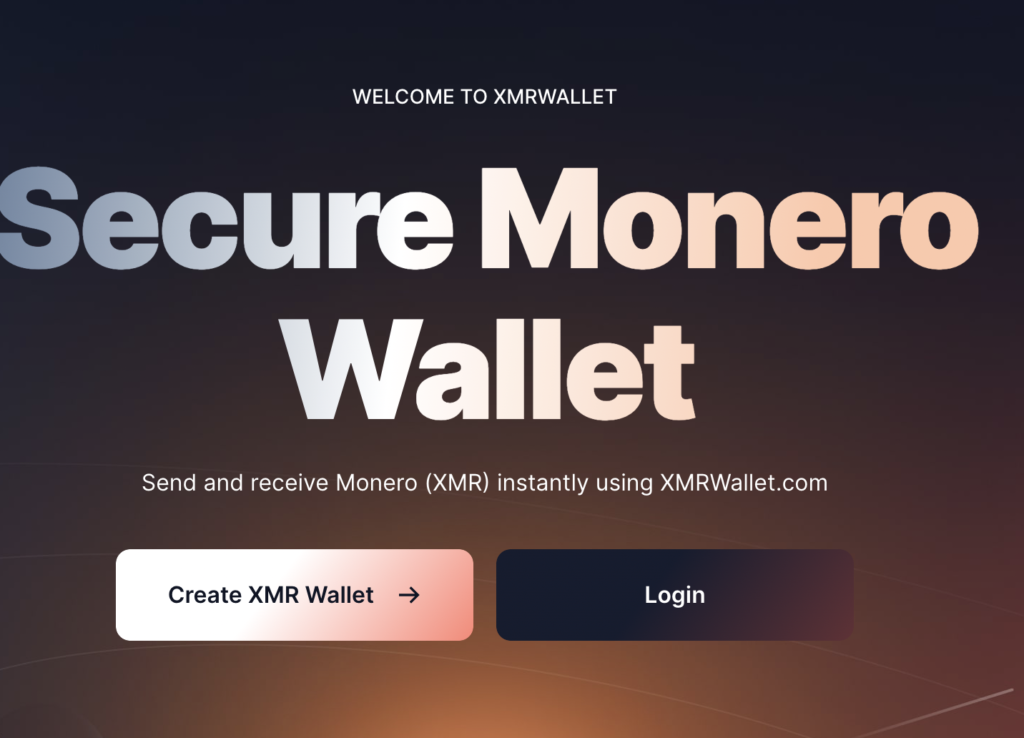
It only takes a few clicks, start by clicking “Create XMR Wallet.”
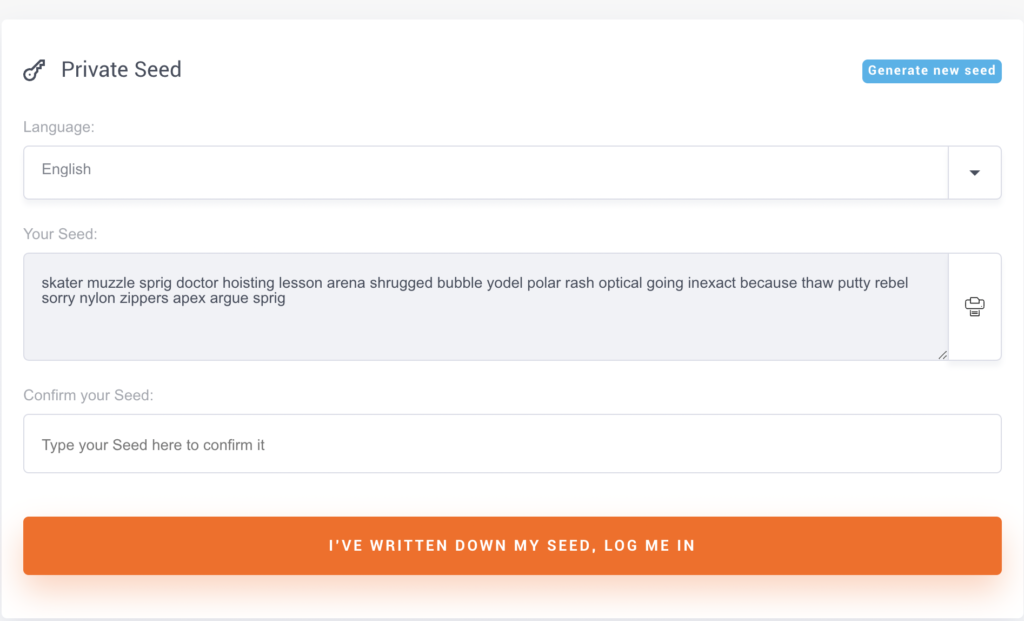
And, we have a Monero wallet and can begin receiving and sending funds!
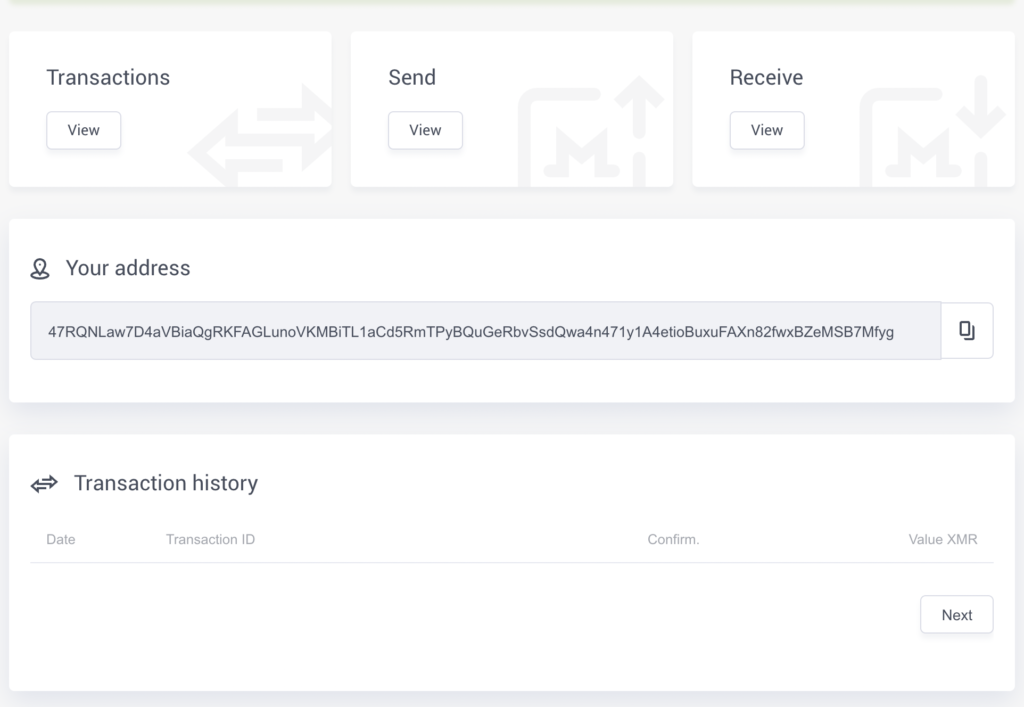
Much easier than making a bank account, right? That’s it, we’re done!
Before we move on, a quick note. You may have noticed this tidbit of advice on the XMRWallet website:
Treat XMRWallet like you will treat your actual wallet. Don’t store large amounts in it. If you’ll use Monero long-term, create an account. Store your private key in a safe place and only use it once.
– XMRWallet safety warning
XMRWallet is smooth for pentesters who need a wallet quickly. If you want an even more realistic simulation, you should set up your wallet the way a bad actor would, with everything running locally.
You can get started running Monero locally here: Downloads | Monero – secure, private, untraceable
Installing the cryptominer on a hacked machine
Once you’ve pwned some systems in a network, you need a Monero miner to run on the infected machines. The easiest to set up is Nanopool | Monero. Download the miner for the appropriate system onto the victim machine.
If you do this on Windows, you’ll have to deal with Windows Defender.
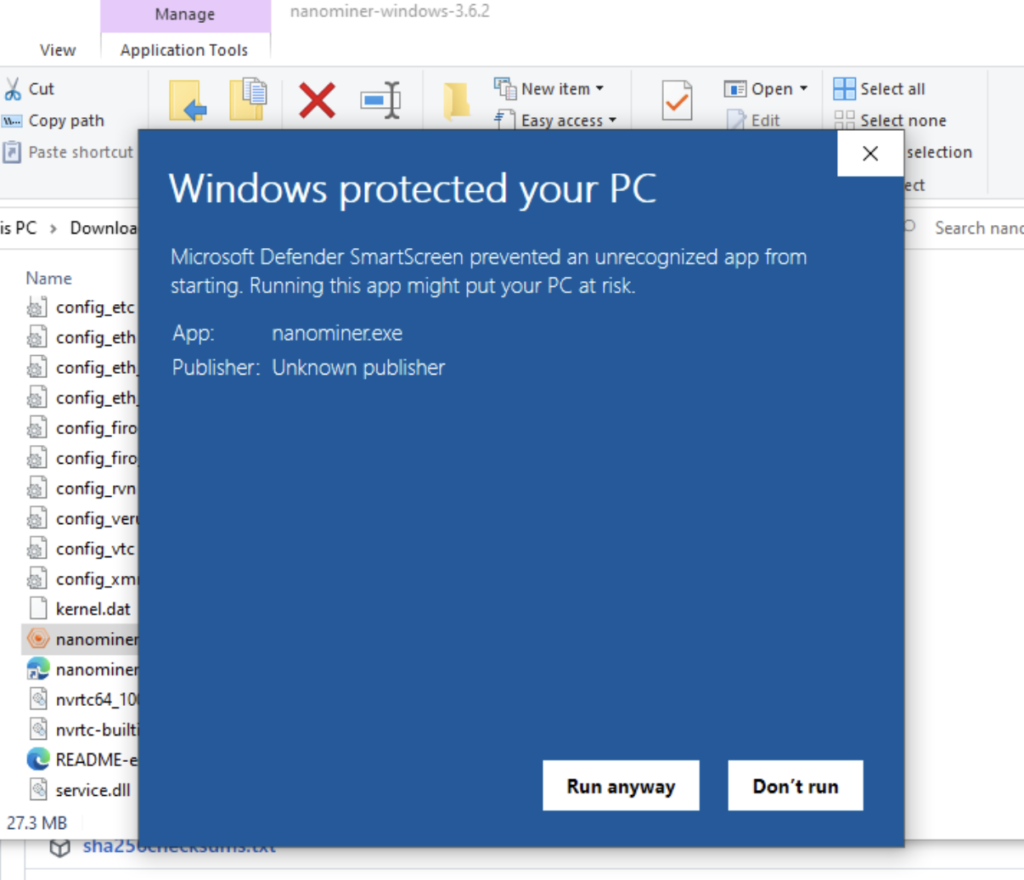
You can use msfvenom or whatever your usual strategy is to evade antivirus. But if it’s Linux, antivirus won’t be an issue.
To set up the miner, edit the config file to use Monero and point it to your wallet.
wallet=<your wallet address>
coin=XMROnce you’ve edited the configuration, run the miner and it will begin mining Monero and sending them to your wallet. By the way, the miner has a lot of cool features. For example, it can detect other miners and has a web interface.
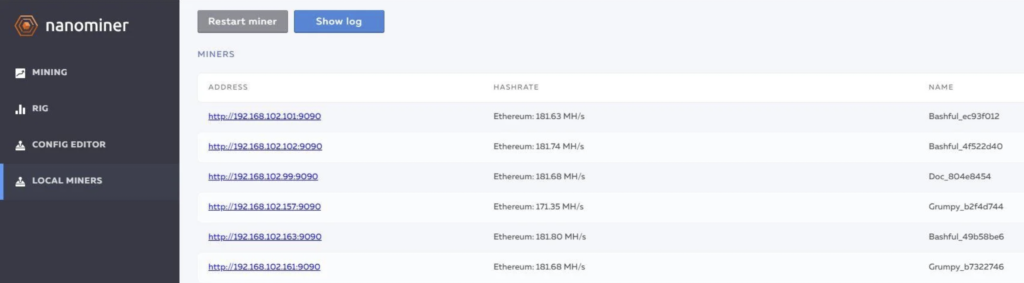
You can learn about more advanced features of Nanominer from the README: https://github.com/nanopool/nanominer/blob/master/README.md
Play around to see what features are useful for you. Congrats, if you get to this point, you succeeded at cryptojacking!
The math of cryptojacking
When showing a client your work, money talks. You can tell them exactly how much money an attacker would make. Because their servers are normal computers, they weren’t made to mine crypto. Thus, each computer will make about two dollars worth of Monero per day.
The formula is simple: profit = # of machines × $2 dollars
If you can get the miner on an entire network of 1,000 computers, that’s $2000 per day for the attacker. Not bad! Very efficient systems, like machine learning and mainframes, can make a lot more.
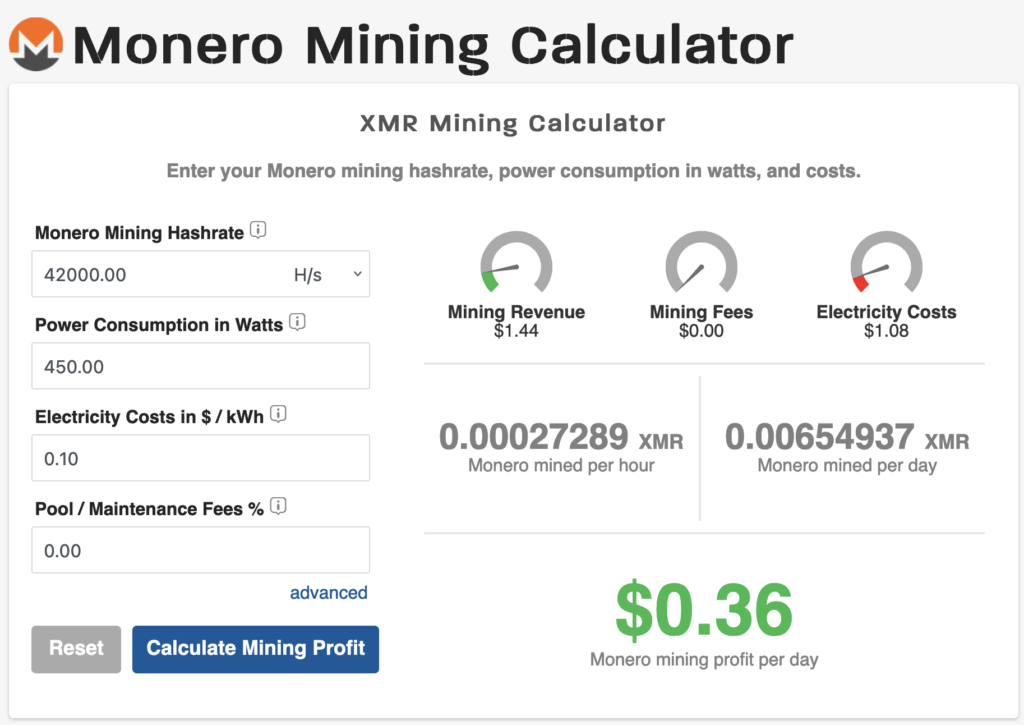
Lots of free apps calculate the profit of mining, just look up “Monero profitability calculator” and use whichever option you find the most friendly.
Tools like Shodan let attackers scan the whole internet to look for machines that they can infect with miners. Thus, even small devices are at risk of cryptojacking.
Why use cryptojacking in a pentest?
Have you ever argued with a client about the impact of an attack? When you hack a machine that doesn’t have anything valuable to exploit, clients tend to think securing it must not be a big deal. By mining crypto on low-value machines during a pentest, you show that all systems have value and need strong security.
Now that crypto is more mainstream, clients are open to ideas like crypto-themed audits. For example, blue teamers stash crypto wallets all over the network. You show you’ve pwned them by stealing the stashed coins. Clients who want to teach their workers about crypto security tend to love this idea. What better way to prove you accessed a machine than by stealing crypto from a wallet that the admins hid there?
Some adventurous pentesters have even let clients pay for a pentest this way – by letting the pentester keep the crypto they found throughout the network.
But at the end of the day, the only reason you need is this: because attackers do it. The point of red teams is that to audit for security issues, we need to think like real attackers. That means copying their tactics as closely as we can. Cryptojacking is one of those tactics. So it should be a core part of any pentest that claims to work like a real attack.

David Mora says
Glorious. Would appreciate a part II going into more coding detail, how to build a script to auto-infect victims and jack them into a botnet, etc.