Hackingloops is back with another Know Your Backtrack Tutorial. In this tutorial, we will be learning DNSMAP Tool for DNS information gathering. DNSMAP, as the name suggests, is DNS Network Mapper, which is used for multiple purposes. Basically, DNSMAP is an passive Network Mapper, often called a sub domain brute force tool. This tool is mainly used by penetration testers and hackers for DNS and sub domain information gathering. It is similar to most other DNS information gathering tools except for a significant feature.
 |
| DNSMAP Tutorial KYB 3 Hackingloops |
- Obtain all A records (i.e. IP addresses) associated to each successfully brute forced sub domain, rather than just one IP address per sub domain.
- Abort the brute forcing process in case the target domain uses wildcards.
- Ability to run the tool without providing a word list by using a built-in list of keywords.
- Brute forcing by using a user-supplied word list (as opposed to the built-in word list).
- Saving the results in human-readable and CSV format for easy processing.
- Improved built-in subdomains wordlist.
- New bash script (dnsmap-bulk.sh) included which allows running Dnsmap against a list of domains from a user-supplied file. i.e.: brute forcing several domains in a bulk fashion.
- Bypassing of signature-based Dnsmap detection by generating a proper pseudo-random sub domain when checking for wildcards (Unique Feature).
cd /pentest/enumeration/dns/dnsmap/
./dnsmap google.com
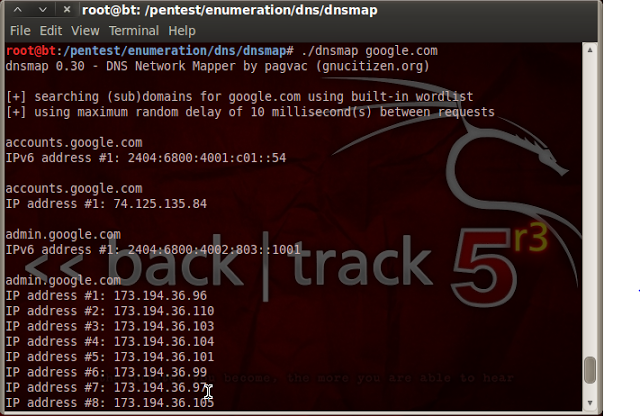 |
| DNSMAP Tutorial – 1 |
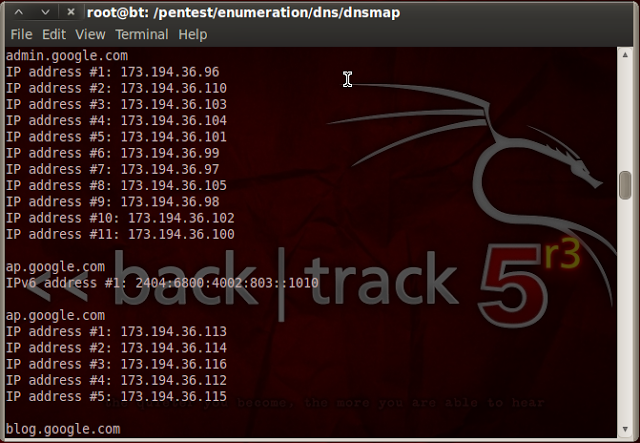 |
| DNSMAP Tutorial – 2 |
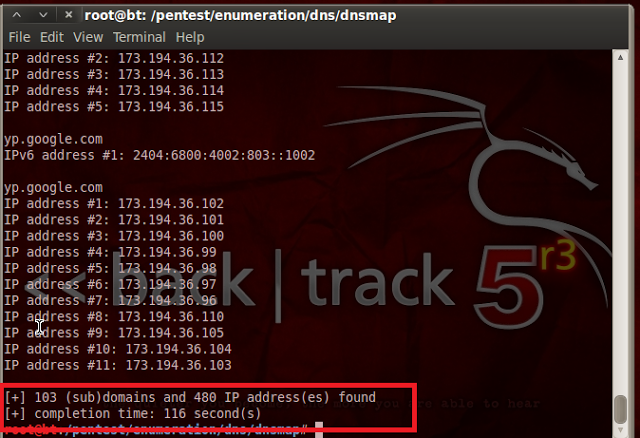 |
| DNSMAP Tutorial – 3 |
-w <wordlist-file>
Input file to use for brute force
-r <regular-results-file>
Export results as text format
-c <csv-results-file>
Save files as csv format
-d <delay-millisecs>
Maximum delay (in ms) between 2 DNS lookups(default: 10 ms)
-i <ips-to-ignore>
Useful if you’re obtaining false positives
./dnsmap google.com -w yourwordlist.txt -r /tmp/domainbf_results.txt
./dnsmap google.com -r /tmp/ -d 3000
./dnsmap google.com -r ./subdomainbruteforce_results.txt

Leave a Reply