Urbit is a mysterious networking technology that’s had the techie underground conflicted for decades. Is Urbit the future of the internet, or a backwater of weirdos too controversial for the normal internet? In this article, we’ll ignore all of the politics and focus on the benefits (and drawbacks) of Urbit for hackers.
Like any cutting-edge tech, Urbit has unique strengths and weaknesses that hackers can leverage. Urbit’s unique architecture makes it ideal for certain hacking tasks, but horrendous for others. Let’s start so you can see what I mean!
Learn the basics of Urbit for hackers
Just like the “old internet” we all know and love, learning Urbit involves mastering a deep tech stack. However, unlike the normal internet, the Urbit Foundation offers a free developer bootcamp called Hoon Academy to anyone who wants to hack on Urbit.
Although this article will give you an overview of what you can do as a hacker on Urbit, Hoon Academy will take you the extra mile and go in depth on every skill.
After you sign up for Hoon Academy, you should go to tlon.io to sign up for Urbit. It’s a free service where they give you a free “Urbit computer” that lets you join groups. I recommend the Urbit Security Fanclub, which you can find (on Urbit) here: ~motluc-nammex/h00ncr3w.
If you’re still having trouble, you can ask for Urbit related help in 13channel’s official Urbit support thread: http://13channel.crabdance.com/b/thread/104.html.
Apps on Urbit consist of two parts:
- Frontend, usually made with React or Sail (a markup language)
- Backend, made with Hoon
Offensive security
Attacking Urbits is easy (for now!). It’s a new technology, and the Urbit Foundation is still working on security. So it’s pointless to talk about offensive security against Urbits at this stage in the network’s growth.
I’d rather tell you about something much more special: how to use Urbit to attack other computers. Among Urbit’s offensive capabilities, the one that stands head and shoulders above the pack is the Moon is a Harsh Mistress (MiaHM) attack.
More of an architecture than an attack, it involves setting up a large number of Urbit’s “moons”, which the main Urbit ship can command and control. Then, the Urbit moons launch a DDoS attack on a target. Typically, in the wild, the moons will live on machines infected with the botnet via malware. However, pentesters can also launch a MiaHM attack to stress test infrastructure.
Of course, attacking Urbits is sometimes necessary, so let’s briefly go over that as well.
Urbit for hacking other people!
Urbit backends are prone to a number of attacks, but if you’re new to Urbit, the frontend usually has the easiest issues to exploit. Most Urbit apps use React, which means XSS is the easiest route. For an example of an XSS attack against an Urbit app, check out our article about Urbit appsec: hacking Urbit apps.
Since best practices for Urbit apps are still in development, it’s a really good platform to experiment with. Unlike old fashioned web dev, where devs have decades of mass usage to guide standards, Urbit offers a freshness and freedom that makes a great space for hacking and play.
Defending yourself
As we mentioned before, Urbit still lacks some pretty major security features. You can find their roadmap for working on these features here: Urbit roadmap for better security. Going through the list, we see that appsec and DoS prevention are in the works still.
Yet, there’s much you can do as a user to make your Urbit relatively safe. For example, to make up for the lack of appsec, you can run apps on different moons, making it so they can’t access each other. Also, you should follow usual Linux tips for hardening the server you run Urbit on. To start out, check out our guide on making Kali Linux more secure: https://www.hackingloops.com/safety-kali-linux/.
Blue team tasks like server hardening are great to pursue, even if you normally prefer red team and pentesting. Why? Because you make yourself more familiar with the defenses that you, as a hacker, will have to work around. In the end, blue team and red team share a lot of knowledge. Learning about one makes you much better at the other, and many red teamers begin in defense.
One final note about defending an Urbit from threats and attacks: many Urbit hosting platforms offer built-in security options that make you safer. For example, the biggest hosting platform for Urbit is Tlon. Take a look at their security settings:
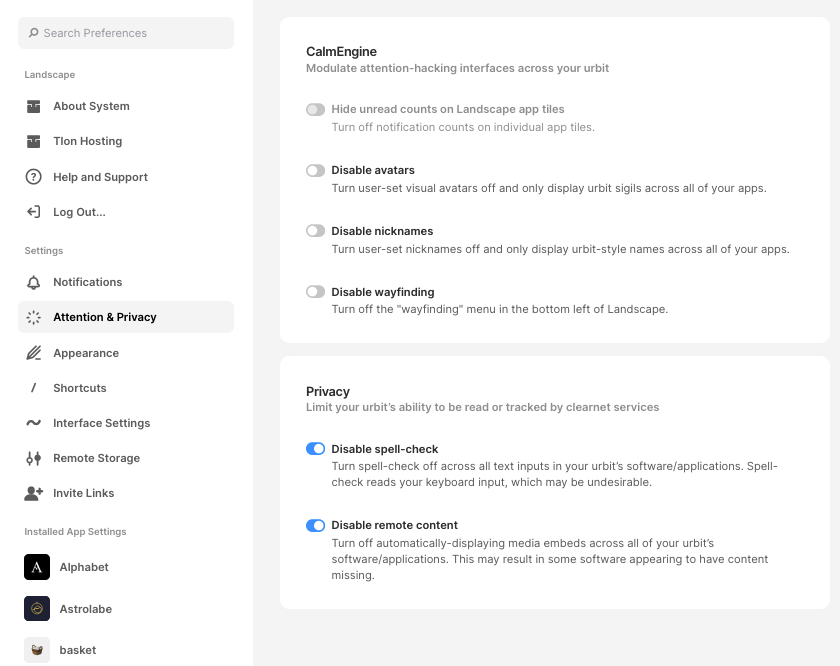
And the devs say that more safety options are on the way! Check your hosting service to see what options they have. The most important option is “Disable remote content” because loading remote content can harm your privacy. When you load a remote image, the image host can see your IP.
Learn more about Urbit for hackers
Urbit’s world goes deep, and learning enough to start hacking can feel intimidating. It’s sort of like when you first start learning about tech, and have to understand TCP/IP, HTTP, browsers, Javascript, Python, Linux, Windows, and so on. Only years of experience make these concepts seem like “basics”. Urbit is just as complicated and deep.
Luckily, the Urbit community has great teachers, and they’ve developed some of the best learning content in the tech world. Check out the resources below to dive deeper into this fascinating world.
- Hoon School: Learn Hoon, Urbit’s programming language.
- Urbit on Wikipedia: Overview of Urbit from a web 2.0 point of view.
- Who pwns the stars? A proposal for appsec on Urbit.
- Urbit, the good, the bad, and the insane: A “neutral” article that attempts to show the value of Urbit, from a critical point of view.
Learning Urbit often becomes quite addictive. The architecture is exciting, and the people are smart and friendly. As interesting as the essays above are, the real way to learn is by doing. So join the network, find a group you like, and start hacking!
I promise you’ll be an Urbit master in no time. Happy hacking!

Leave a Reply