If you want to learn hacking, there’s no way around it: you need to learn networking. Maybe you needn’t master the ins-and-outs, but you at least need to grasp the basics and have a working understanding. Why? Because machines talk to each other through networks. Most hackers exploit machines remotely, so you need to traverse a network to reach your target. Once you pwn a box, you’ll find other machines it has access to via the network. Networking often scares new hackers. It seems like a complex topic that takes too much time to master. For that reason, we made this guide to networking for hackers.
As a hacker, you only need certain parts of networking to hack effectively. So open up your mind and get ready to learn!
Domain names and IP addresses: networking fundamentals
When you access a website, you do so through a domain name, like hackingloops.com or wrongthink.net. Secretly, your machine converts that name into a special number (called an IP address). Then, this number allows you to access the server that hosts the website on the internet.
You can use the nslookup command to find manually find the IP address that goes with a domain name. Try it yourself on the command line like so.
$ nslookup hackingloops.com
Address: 104.21.13.47Pretty easy, right? There are two kinds of IP addresses: IPv4 and IPv6. Why two? Because the internet began to run out of IPv4 addresses! So we needed a new version that would offer many more addresses and prevent this issue. If you’re curious about what happened to versions one, two, three, and five, read the history here: https://en.wikipedia.org/wiki/List_of_IP_version_numbers#History.
IPv4 addresses have four 8 bit numbers separated by dots, like so:
104.21.13.47Whereas an IPv6 address consists of hexadecimal numbers connected by colons:
2606:4700:3036::6815:1c28If you lookup the IP address if a site with nslookup, you’ll almost always get an IPv4 address. But you can always request to only see the IPv6 address of a site using the more powerful dig command.
dig -t aaaa wrongthink.net
[...]
wrongthink.net. [...] 2606:4700:3036::6815:1c28Special IP addresses
Now you have a basic idea of how IP addresses work. But you should also know that there are certain special addresses. As a hacker, you run into these addresses all the time, so you might as well memorize them.
127.0.0.1
The “loopback” address, or localhost. Those are just fancy terms that mean “the machine you’re on right now”. The loopback address, or 127.0.0.1, is the IP address a machine uses to refer to itself. For example, if I wrote a web server and wanted to access a database on the same server, I’d use this address.
192.168.*
Any address beginning with 192.168 refers to a device on your local network. As in, it’s connected to the same router. In fact, your router usually resides at 192.168.0.1. Later in this guide, we’ll show you how to scan your local network to see what devices are connected.
8.8.8.8
When you look up a domain name to get its IP address, you ask a special server called a nameserver. Your OS usually comes with some nameserver IPs built into the machine. Often, one of the nameserver IPs is 8.8.8.8, which is Google’s nameservers.
When you see this, you can usually just ignore it.
Common networking protocols
IP is a pretty low level protocol. Usually, programs want to do a lot more than simply find other machines. For example, machines might want to chat, send alerts, play a multiplayer game, and so on. To do this, both machines need to speak the same language, so they can interpret incoming data correctly.
Thus, a bunch of protocols serve every imaginable need. Let’s look at some of a few of the most important ones for hackers.
HTTP
HTTP powers websites! Everyone and everything uses the web, making HTTP arguably the most significant protocol for hackers. You don’t need to become a web dev (but it wouldn’t hurt!) to know when to use a GET or POST request, how to code in HTML, and so on.
I really suggest you dive deep into HTTP. Even for devs who don’t hack, this protocol is just so important. Check out MDN’s excellent docs on HTTP to start learning: https://developer.mozilla.org/en-US/docs/Web/HTTP/Overview.
To give you a taste of what raw HTTP looks like under the hood, let’s connect to a site manually. Remember 2606:4700:3036::6815:1c28? That’s the IPv6 address from earlier.
$ nc 2606:4700:3036::6815:1c28 80
GET / HTTP/1.1
Host: wrongthink.net
HTTP/1.1 200 OK
Date: Sun, 14 Jan 2024 03:38:48 GMT
Content-Type: text/html; charset=UTF-8
[...]Try it yourself! The command we’re using, nc, refers to netcat. It’s an extremely useful networking tool for hackers. So you should learn about it, try this guide: https://medium.com/@HackTheBridge/beginners-guide-to-netcat-for-hackers-55abe449991d.
SSH
SSH lets you open a command line on a machine over the internet. For example, you might need to reboot your server. Using SSH, you can connect to it and run the reboot command.
The underlying protocol is actually pretty complex, but you don’t really need to know much about that. It’s enough to know how to use the ssh command, which follows this easy format:
ssh username@domain.exampleThen you have to enter the password. Really, it’s that simple! Some hosts might not let you login with a password, or restrict what IP addresses can login over SSH. But as a beginner, you needn’t worry about any of that yet.
Yep, email runs on network protocols! Actually, it runs on three protocols: SMTP, POP3, and IMAP. No need to worry about those terms yet, though.
Fun fact, you can actually see some of the protocol metadata for your emails using Gmail’s web interface, like so:
Click “Show original”, and you’ll see a bunch of protocol headers.
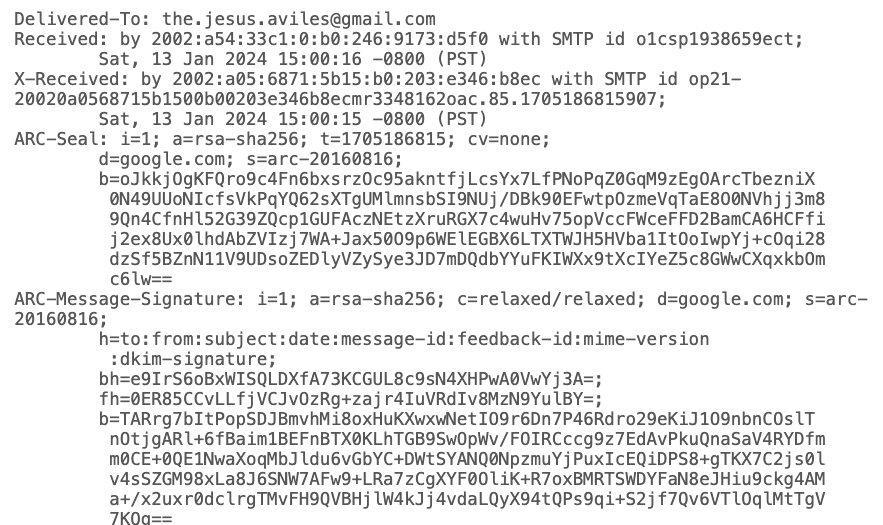
Email gets pretty deep, but if you want to learn phishing and email spoofing, you need to learn how these headers work. Specifically, you’ll need to learn about SPF, DKIM, and DMARC (among others!). Like I said, it gets deep.
Exploring networks
The original hackers weren’t cybercriminals trying to exploit software for financial gain. Rather, they were curious youths exploring phone and computer networks, seeing what weird systems they could find. In the spirit of the hackers of yore, let’s see how you can explore networks using the nmap tool.
The simplest thing nmap does, is show you what ports are open on a machine. Ports allow a single machine to run different services, like a website and email. To connect to a specific service, you specify it’s port number. Let’s see what ports are open on hackingloops.com.
$ ➜ ~ nmap hackingloops.com
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-13 21:46 CST
PORT STATE SERVICE
80/tcp open http
443/tcp open https
8080/tcp open http-proxy
8443/tcp open https-altWe see HTTP, as well as HTTPS (which is the encrypted version of HTTP) as well as some alternatives for both. Not very interesting.
Let’s try something more exciting. What if you had reason to suspect that a hacker had broken into your network. You could use nmap to scan the local network and see what devices are connected!
~ nmap '192.168.0.*'
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-13 21:57 CST
192.168.0.1: Router 1
192.168.0.2: iPhone
192.168.0.3: Macbook
92.168.0.252: Router 2With this command, we see the local IP address and name of every device connected to our network!
Keep learning about networking
Your journey has only just begun! Check out the tips below for how you can dive deeper and master the principles of networking.
- Play networking CTF games.
- Get a free domain from freedns.afraid.org
- Use ngrok to serve a website from your laptop
Networking involves a lot of concepts and and tools, but you’re a hacker, not a network engineer. Use the knowledge from this guide to decide which networking concepts matter most for your work and focus on those.
As always, happy hacking!

Leave a Reply