Overview
The massive global community and security enthusiasts practice website password cracking regularly. Most of the time, it is to test the vulnerability of services that helps services in return. Nonetheless, it takes a great amount of technical knowledge, practice, and patience. Various tools and different variables are required to gain appropriate results. This is where THC-Hydra and Burp Suite comes in handy.
Hacking passwords of online services like website authentication, email, and social media accounts falls under penetration testing. Though cracking or hacking online services is not the same as before. They became much secure & there are more loopholes to go through. This is great for general users but for penetration testers, it means going the extra mile. Hacking tools make things quite easy to test. So, learning penetration testing and hacking online passwords is not tough as it looks.
To use THC-Hydra and Burp Suite for online website password cracking, we are going to use the Kali Linux distro in a VirtualBox. And later proceed with the tools mentioned. Let’s go through the steps of setting the environment up and adequate tools.
There are a few things we are going to need. A Linux distro, Hydra (command line), Burp suite, web browser of choice, and a username and password list.
Step 1: Setting up the environment
In the beginning phase, we are going to install kali Linux in a VirtualBox. Assuming most of the readers here have a virtual machine running. Those of you can proceed directly from 2nd step. We can download Oracle VirtualBox from here and a distro of choice from the official Kali site. Any Linux distribution system will get the job done.
Once VirtualBox is installed, we can open it and click “New”. From here we will fill up basic details like the name of the OS, Type = Linux, and Version = Debian (64-bit). From the setting, we can allocate memory.
Create a virtual hard disk now > VDI (VirtualBox Disk Image) > HDD size as Dynamically allocated > Setup a size.
It is to be noted that the boot order form setting has to be Hard Disk and Optical respectively. The rest will be ticked off as we have no use for them now. For greater experience, we can increase CPU core count and video memory size to max. Once they are done, we can start the VirtualBox and locate the disk image (iso). Now we are ready to proceed to the next step.
Step 2: Preparing Offline Prerequisites
As we will be brute forcing our way into a dictionary attack, a username and password list should be present. Luckily there are tons of password and username dumps on the internet. Yes, we can use those. But running every item on the list will take a long time. And for our brief tutorial, we will make a small list manually.
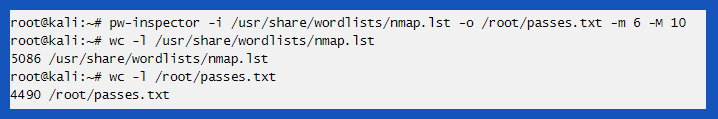
On the shell command line and inside the directory, type in “vi usernames.txt” and for password list “vi passwords.txt” respectively. Inputting any kind of dictionary usernames and passwords can handle the task perfectly.
Step 3: Setup Hacking Tools
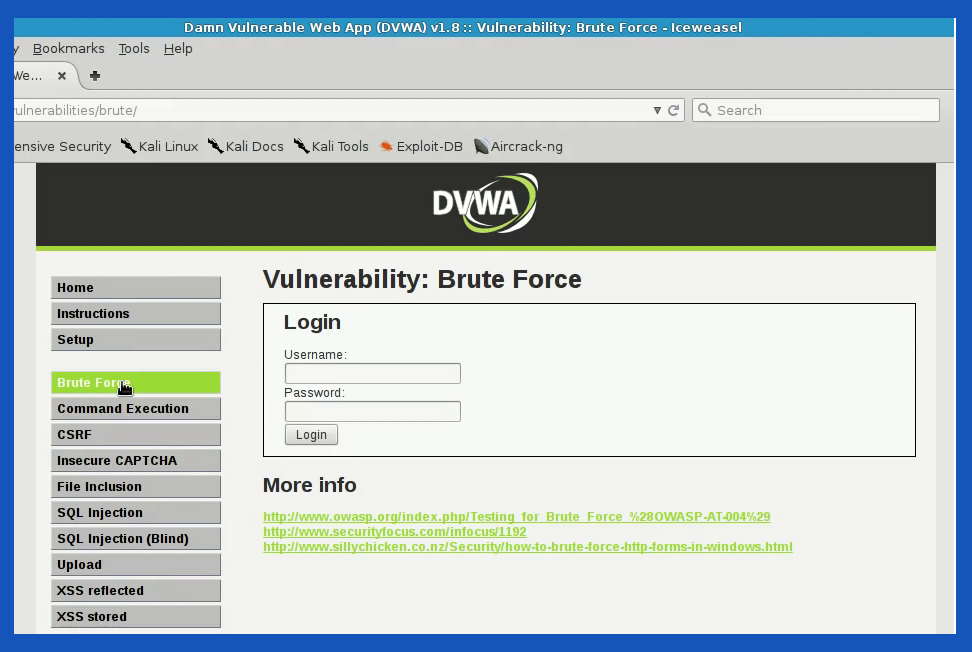
We can use DVWA (Damn Vulnerable Web App) in a local host machine to test our project. From our list of Kali Linux Applications, Password Attack > Online attacks, open hydra regular toolkit.
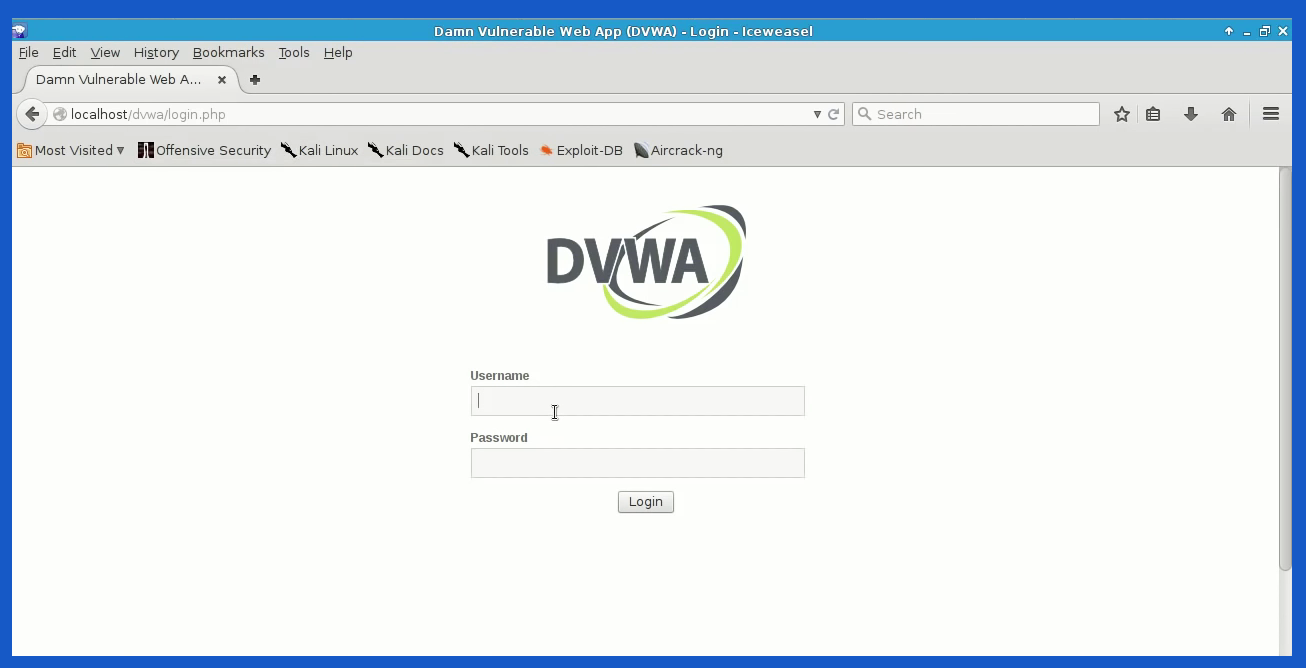
For testing our subject or website a “URL” needs to be listed. We can not test vulnerability on sites without permission as it won’t be legal. And for the demo, we need a platform that is easier to check results. For Burp Suite, it can be downloaded from the official site. And again, for testing, we can use the free version. The community edition cost a few hundred bucks which contain a few extra tools but we’ll not be needing them for this demo. From Kali Linux Applications, Web Applications, open up Web Application Proxies and then burp suite. Burpsuits can be set up with the default settings and they will pick up the best settings available. Once default settings are ticked, we can start the burp suite project.
Step 4: Browser Configuration & Using Toolkits
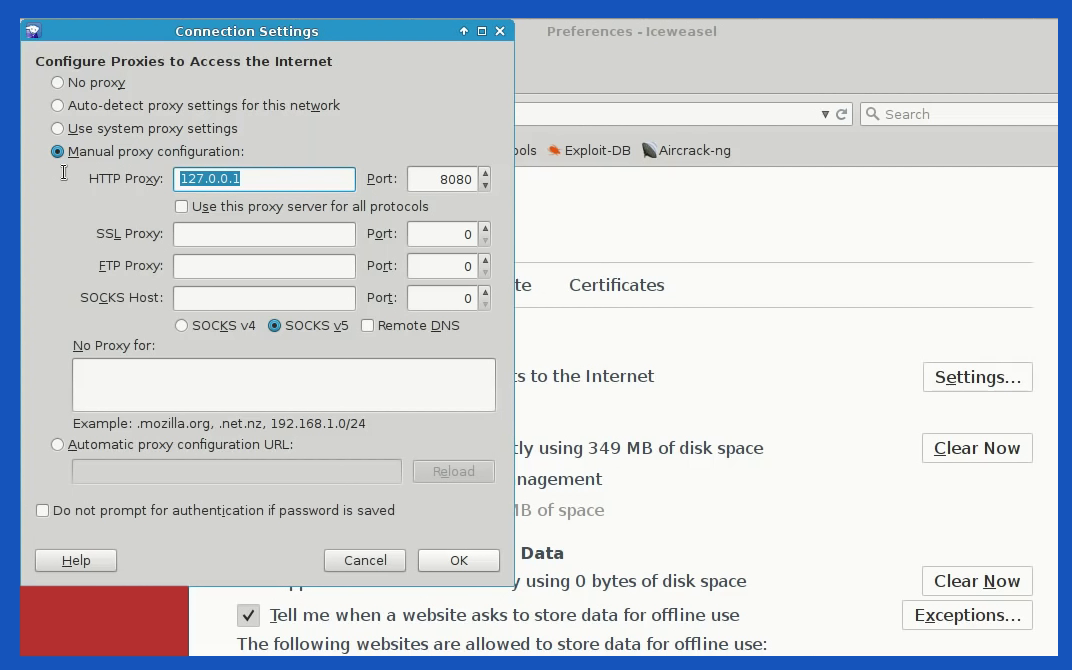
We can use any browser of our choice. Linux comes with a wide variety of choices. For this one, Firefox or Ice weasel works best. Let’s change its proxy setting to localhost with a manual proxy configuration. Manual HTTP Proxy is 127.0.0.1 and for Port, we can use 8080.
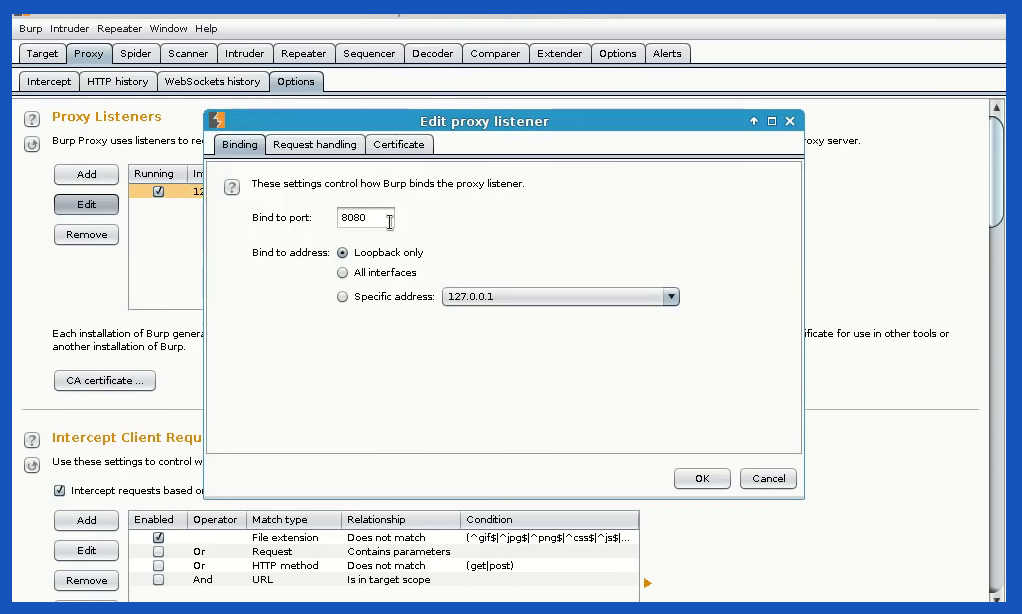
If we check our burp suite application, there are no newlines or messages. But if we hit the wrong id in DVWA, our burp suite picks up the wrong GET request data alongside browser information. It is noted that DVWA security needs to be set as “low”.
From Burpsuite Proxy tab > Raw data, we can copy the request texts and keep them separated in a notepad to use later. Once the data is collected, we can turn Burp Suite’s intercept off and head back to DVWA. It is time to set our browser proxy to default, as the data we need is already collected in the notepad.
It is also possible to test vulnerabilities by creating a small-scale HTTP HTML page and experiment with it. That way we know what we are up against and break our system. No harm no foul.
Step 5: Start penetration testing using Hydra
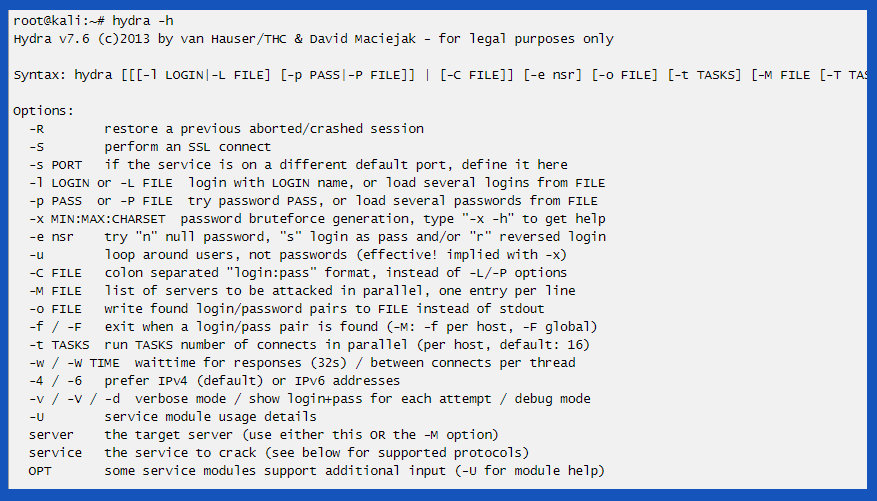
On the command line, simply typing in hydra -help will show us all the commands to run hydra. As hydra is case sensitive, a lowercase -l will use a simple login username.
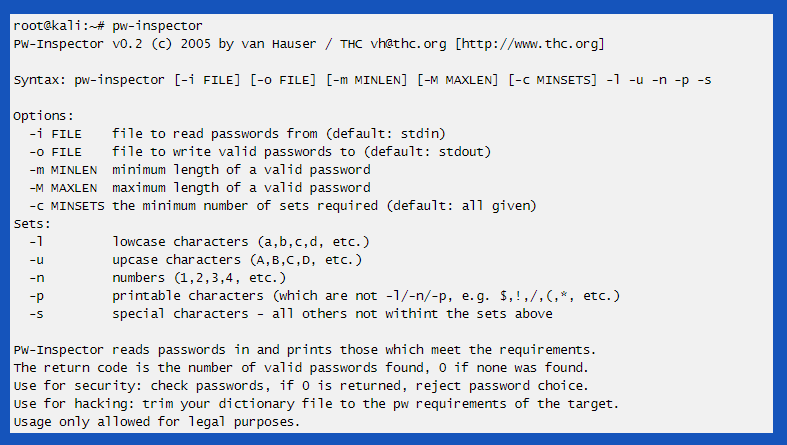
And for dictionary-based attacks which we can collect from various sources. But in our case, we already created a text file with a possible list of usernames.
The correct format is “-L followed by “usernames.txt”. Similar for password. Lower -l is for a single password like “qwerty” or “13345”. -L for larger sessions similar to the text file we created or imported as a dictionary previously.
Key Points:
- For passwords, as we don’t know what it could be, for a dictionary word list, we can use
-P /usr/share/wordlists/passwords.txt
- For username “-1 admin”
- Command syntax as a placeholder
sudo hydra <Usernames/List> <Passwords/List> <IP> <Method>”<Path>:<RequestBody>:<PassList>”
- Primary command syntax
sudo hydra -l admin -P /usr/share/userlist/usernames.txt 10.10.10.43 http-post-form”/files/login.php:username=admin&password=^PASS^:Invalid Password!”
- Copied commands may not work properly, so just in case, remove the quotation marks and manually insert them on the command line.
- Multiple attempts may stop the experiment if taken as spam. Time randomization and breaks are necessary.
Useful Information
- Hydra is sensitive to caps, symbols, etc., and should be handled carefully.
- To save a bit of time, in the burp suite, enable the toggle for a parameter in the repeater tab.
- Building a default project and saving a .json file can be a great friend for future testing.
- Setting up the default intruder payload will also save time.
- Matching and replacing “FALSE2TRUE” in the burp suite gives out some interesting results.
- Sensitive dumps should be handled and saved carefully.
- For the XSS polyglots, add XSS1=”‘–></style></script><svg oNload=alert()>
Summary
Penetration testing is all about skills, patience, and practice. Once we acquire key knowledge, it is usable in real-world applications. But testing on services without permission may get testers into trouble. So, we suggest staying within boundaries and respect privacy. For wild guessing, it is recommended to use THC-Hydra forms. Hope this guide will give a head start in your hacking carrier.

Leave a Reply